Why Hybrid Teams Win: Code Developers x No‑Code Developers
High-performing digital teams blend the strengths of code developers and no code developers. No‑code accelerates validation and delivery; custom code unlocks differentiation, performance, and scale. Together, hybrid teams ship faster, reduce risk, and create future‑ready foundations that don’t paint you into a platform corner.
"By 2025, 70% of new applications will utilize low-code or no-code technologies." - Source
At Trikon Tech, we help you decide when to build and code, when to configure, and when to combine - so you move from idea to impact without rework or technical debt.
The collaboration gap we’re closing
Bridge code developers and no code developers to ship faster, safer, and with fewer rework loops.
Position hybrid teams as a competitive advantage when you need both speed (no‑code) and differentiation (custom code).
What this Collaboration Playbook covers
Practical operating model for when to build and code, when to configure, and when to combine.
Best practices for shared component libraries, handoffs, change control, and data governance.
Templates and checklists you can adopt immediately.
Who this is for
Non‑technical founders, product managers, operations leaders, and marketers partnering with engineering.
Technical leads integrating no‑code platforms into modern stacks without creating shadow IT.
Outcomes you can expect
Faster delivery of high‑confidence features, clearer ownership, lower long‑term costs, and scalable architecture that respects both sides’ strengths.
Operating Model: When to Build in No‑Code, Custom Code, or Both
To move faster without sacrificing quality, align code developers and no code developers around a clear operating model. Use no‑code for speed and iteration; use custom code for differentiation, performance, and control; combine both when you need to build and code while keeping delivery velocity high.
The decision framework (speed vs. differentiation vs. risk)
Map features along axes: time‑to‑value, regulatory/infosec risk, performance/latency needs, and IP/differentiators. Decide based on the most demanding axis.
Use no‑code for CRUD workflows, internal tools, marketing sites, and experiments where speed and iteration matter most.
Use custom code when requirements exceed platform limits (complex branching logic, strict SLAs, real‑time processing, deep/legacy integrations, heavy data workloads).
Use hybrid (build and code + no‑code) for headless front ends, orchestrations, and progressive decoupling. Keep commodity layers in no‑code, move specialized services to code.
Decision matrix
Capability | Complexity | Compliance/Security | Performance/Scale | Time‑to‑Market | Recommended Path (No‑Code / Code / Hybrid) |
|---|---|---|---|---|---|
Authentication | Medium–High (SSO, roles, MFA) | High (PII, OAuth/OIDC) | High (global sessions) | Moderate | Hybrid (managed auth + custom policies/roles) |
Marketing Landing Pages | Low | Low | Moderate (CDN) | Fastest | No‑Code |
Internal CRM Workflow | Low–Medium | Medium (access controls) | Low–Medium | Fast | No‑Code |
Real‑time Notifications | Medium | Medium | High (low latency, fan‑out) | Moderate | Hybrid (event service in code + no‑code triggers) |
Pricing Engine | High (rules, simulations) | Medium (auditability) | High (cache, concurrency) | Slower | Code |
Data Syncs | Medium (ETL/ELT, mapping) | Medium–High (data residency) | Medium (batch vs. stream) | Moderate | Hybrid (code integration layer + no‑code orchestration) |
Fusion teaming: shared accountability across disciplines
Define joint ownership of outcomes (business + engineering) and clear decision rights for when to configure vs. build and code.
Establish a common backlog and one roadmap with tagged work types (no‑code, code, hybrid) so priorities and handoffs are unambiguous.
Align acceptance criteria across roles: UX, compliance, data, and SRE sign‑offs for high‑risk changes.
"A fusion team blends technology or analytics with business domain expertise and shares accountability for business and technology outcomes." - Source
Tooling alignment
Agree on the golden path: approved no‑code platforms, code stacks, API standards, and observability (logs, traces, metrics) used by both sides.
Document platform boundaries and “escape hatches”: when/how to move from no‑code modules to code services, including data models, API contracts, and rollback plans.
Standardize integration patterns: event-driven messaging, webhooks, and API gateways to keep no‑code apps and microservices loosely coupled.
Enforce change control: versioned components, environment promotion (dev/stage/prod), and shared dashboards for uptime, performance, and error budgets.
Trikon Tech can implement this operating model end‑to‑end - so your hybrid team ships high‑confidence features faster, with clear ownership and a scalable foundation.
Shared Component Libraries and Design Systems (Code + No‑Code Parity)
A unified design system keeps code developers and no code developers aligned visually and functionally - so every release looks consistent, ships faster, and scales cleanly across stacks.
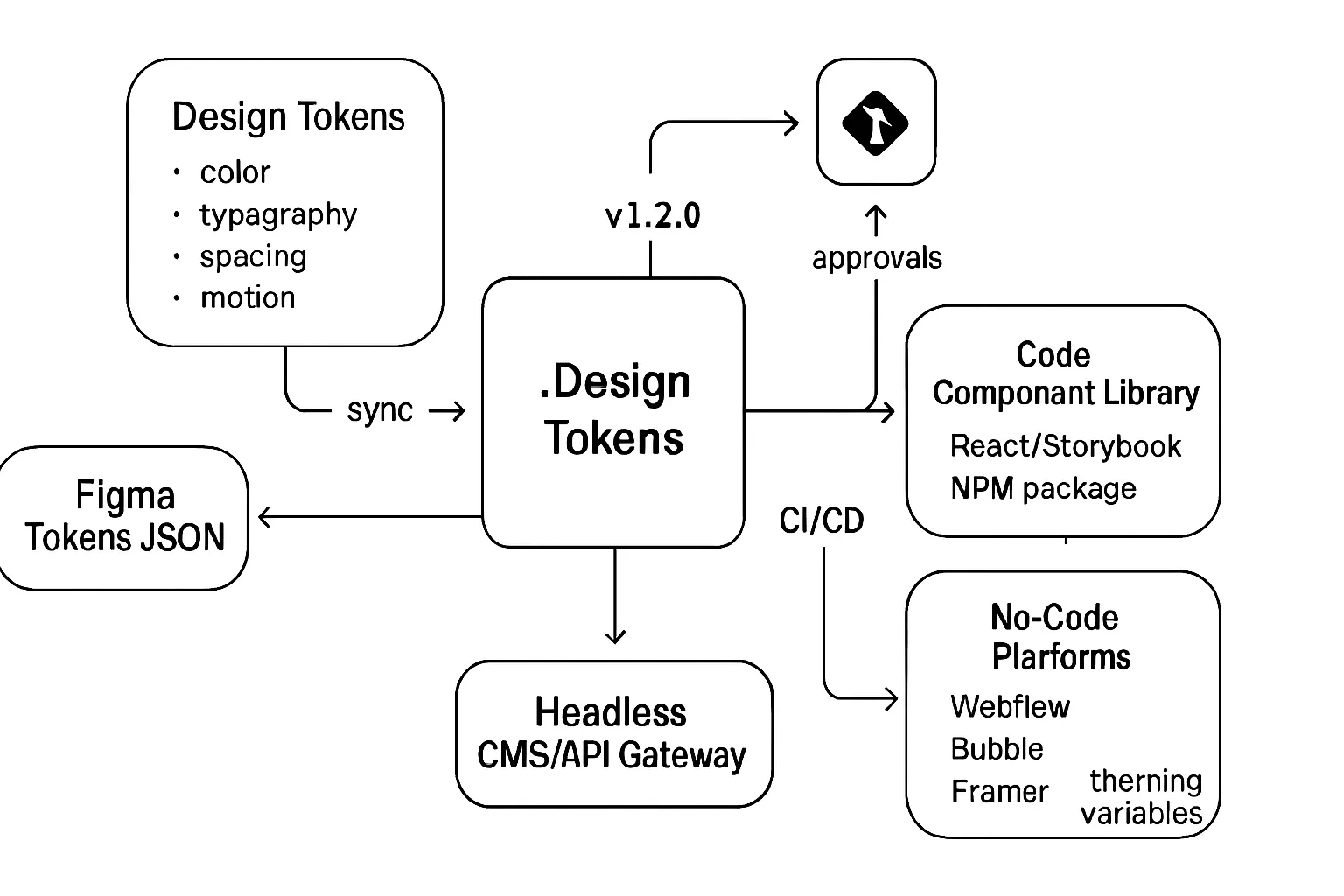
Design tokens as the single source of truth
Centralize color, typography, spacing, and motion tokens in a repository (JSON/YAML) with semantic naming.
Sync tokens to both code repos (e.g., via Style Dictionary) and no‑code theming (CSS variables, design tokens in Webflow/Bubble/Framer).
Automate token release versions (e.g., v1.2.0) with CI so no‑code builders and code developers receive identical updates, with changelogs and diffs for safe adoption.
Shared UI components across stacks
Mirror critical UI elements: buttons, inputs, cards, nav, modals - implemented in React/Vue and mapped to no‑code components/blocks for visual parity.
Publish interactive documentation (Storybook) and usage guidance that no‑code teams can reference when configuring components.
Maintain accessibility contracts across both worlds: ARIA attributes, focus states, keyboard navigation, and WCAG contrast rules included in component specs and token palettes.
Content and schema parity
Define content types, fields, and validation rules once; sync to a headless CMS for no‑code and to a typed schema (OpenAPI/GraphQL) for code.
Enforce schema migration discipline: version content models, provide migration scripts, and validate with CI to prevent drift between CMS and services.
Standardize rich text, media handling, and localization keys so content renders consistently across code and no‑code surfaces.
Governance
Version components and tokens; publish release notes, adoption guides, and deprecation timelines so teams can plan upgrades.
Gate changes with approvals (design, accessibility, engineering) and automated checks (visual regression, a11y linters).
Maintain a single registry for components (npm package + no‑code library) and tag each with compatibility metadata to ensure safe mix‑and‑match assembly.
Rock‑Solid Handoffs: From Brief to Build (and Back)
"PMI reports that 5.1% of project investment is wasted due to poor requirements management (US$51M per US$1B)." - Source
A crisp, consistent handoff model lets code developers and no code developers move from brief to build - and back for iterations - without rework, surprises, or missed requirements.
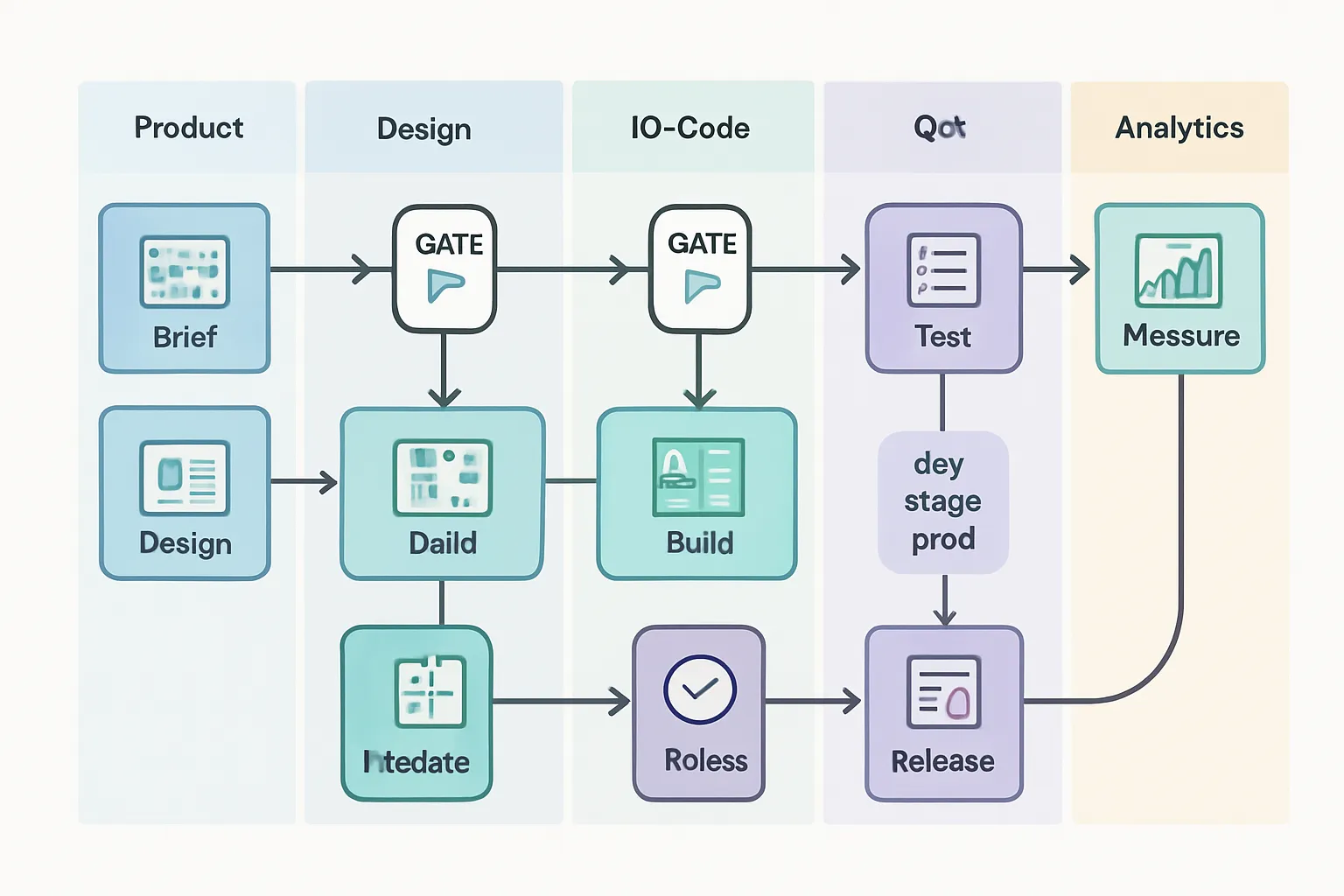
Define Done for both sides
Acceptance criteria templates that cover UX, performance SLAs, security controls (authZ/authN, PII), analytics events, and rollback steps.
API contracts (OpenAPI/JSON Schema) versioned in the repo and linked to tickets and no‑code workflows; include example payloads and error catalogs.
Observability baseline defined up front: logs, traces, metrics, and dashboards required for release.
The hybrid handoff checklist
Include artifacts: user story map, wireframes/mockups, data model and migrations, API specs, test cases (unit/integration/UX), analytics plan (events, schemas), rollout/rollback plan.
Clarify ownership of staging data, seeded test users, fixtures, and environments across both platforms (dev/stage/prod).
Capture platform constraints and escape hatches (what stays no‑code vs. what moves to build and code).
Progressive delivery
Use feature flags and phased rollouts; enable canaries and percentage rollouts by audience or environment.
Run no‑code and code versions in parallel when de‑risking migrations; mirror events and compare metrics before cutover.
Define go/no‑go and rollback criteria tied to objective thresholds (error rate, latency, conversion, data integrity).
Feedback loops
Establish demo cadence (weekly/bi‑weekly) with side‑by‑side views of no‑code and code paths.
Run retros focused on hybrid issues: where platform limits caused workarounds, handoff friction, or schema drift - and capture decisions in docs.
Close the loop with analytics reviews to confirm outcomes against acceptance criteria and business KPIs.
RACI matrix for hybrid handoffs
Activity | Responsible (No‑Code) | Responsible (Code) | Accountable | Consulted | Informed |
|---|---|---|---|---|---|
Brief Creation | No‑Code Lead / Product Ops | Tech Lead (feasibility) | Product Manager | UX, Data/Analytics, Security | Stakeholders, Support |
Data Modeling | No‑Code Architect / CMS Admin | Backend Engineer / Data Engineer | Engineering Lead | Product, Analytics, Privacy | QA, Support |
API Contract | No‑Code Lead (integration needs) | Backend Lead (OpenAPI/JSON Schema) | Solution Architect | Security, DevOps | Product, QA |
QA/Test | No‑Code Builder / QA | SDET / QA Engineer | QA Lead | Product, Data | Support, Success |
Release | No‑Code Lead (publish) | DevOps / Release Engineer | Engineering Manager | Product, Security | Marketing, Support |
Analytics Setup | Growth/No‑Code Analytics | Data/Analytics Engineer | Product Analytics Lead | Privacy/Legal | PMs, Execs |
Rollback Plan | No‑Code Lead | SRE / DevOps | Incident Commander / Eng Lead | QA, Security | Exec Sponsor, Support |
Trikon Tech operationalizes this model so your hybrid team ships high‑confidence features quickly - with clear ownership, measurable quality, and safe rollback at every stage.
Change Control and Release Governance for Hybrid Teams
Robust governance lets code developers and no code developers ship quickly without losing control. Standardize how changes move from idea to production - across both code and no‑code - so audits are effortless and rollbacks are safe.
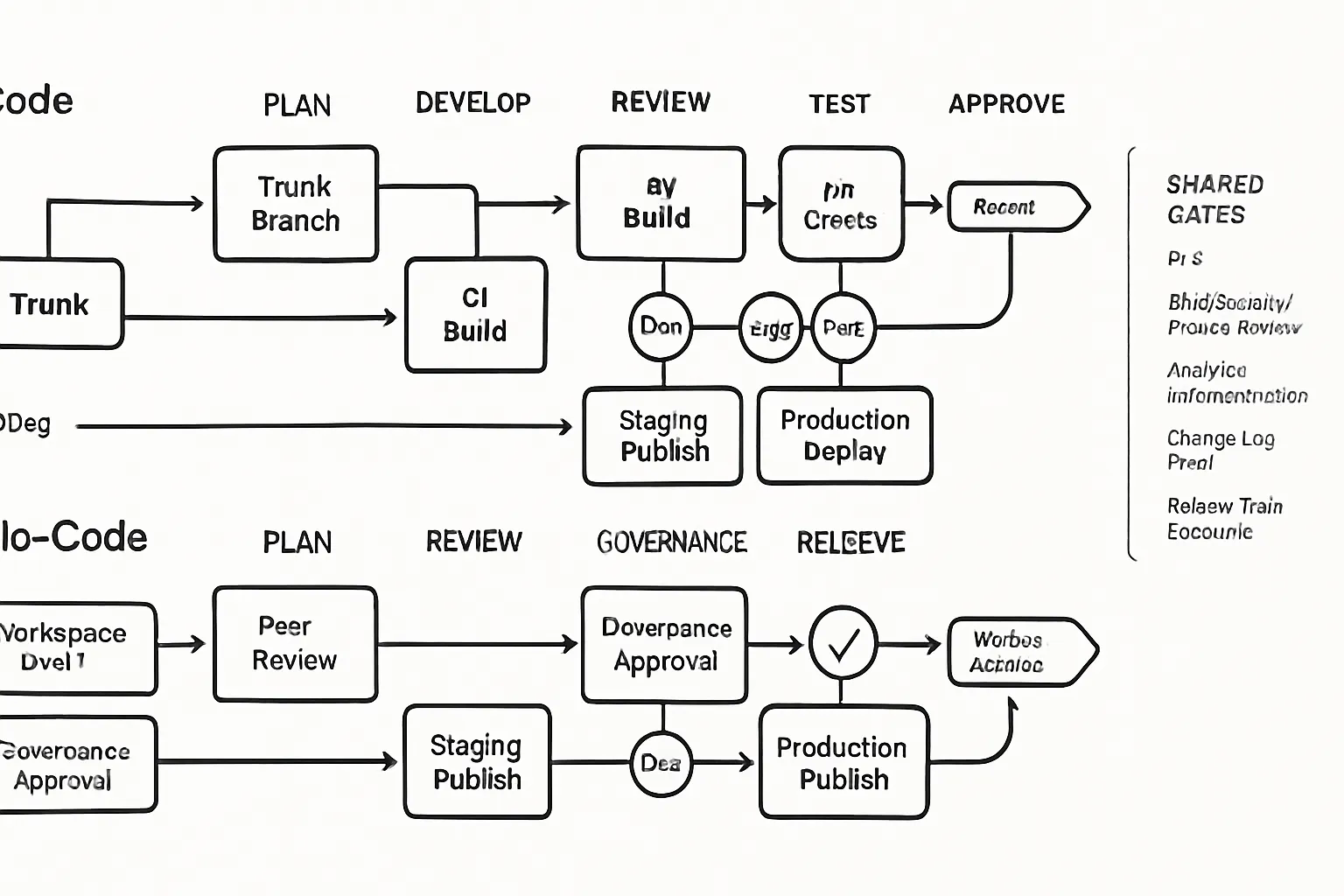
Branching, versions, and environments
Trunk‑based development with short‑lived branches; semantic versioning for components and no‑code packages with changelogs.
Align environments Dev → Staging → Production across code repos and no‑code workspaces; enforce promotion rules and data separation.
Tag releases across both stacks so incidents can be traced to specific versions and change sets.
Approvals and risk reviews
Lightweight RFCs for risky changes (security‑sensitive, schema‑breaking, user‑visibility); include context, alternatives, and blast radius.
Security and privacy checks embedded in the workflow: SAST/DAST, dependency scanning, secrets checks, and data handling reviews for no‑code connectors.
Require dual‑approval at high risk gates (engineering + business) with audit trails.
Release trains and rollback
Cadenced release trains with an emergency lane for hotfixes; publish calendars so stakeholders know what’s landing when.
One‑click rollback on both platforms: feature flags and git revert for code; version restore for no‑code with pre‑validated snapshots.
Canary or blue‑green strategies for code; staged audience rollouts for no‑code to de‑risk launches.
Auditability
End‑to‑end change logs link commits, no‑code revisions, tickets, RFCs, test runs, approvals, and release notes in one place.
Immutable audit artifacts stored per environment; include who, what, when, and why.
Monitoring and analytics tied to each release to verify impact and support post‑release reviews.
Trikon Tech operationalizes this governance so your hybrid team ships fast, safely - and with confidence at audit time.
Data Architecture, Security, and Compliance in a Hybrid Stack
Hybrid teams win when data is consistent, secure, and observable across both custom code and no‑code platforms. Trikon Tech helps code developers and no code developers align on a single, governed data backbone - so you can build and code with confidence at scale.
"The principle of least privilege dictates that users and programs should only have the necessary privileges to complete their tasks." - Source
Unified data model and contracts
Establish a canonical data model with shared schemas and IDs; manage in a schema registry with versioning and deprecation policies.
Treat APIs as the contract between platforms: publish OpenAPI/GraphQL specs, enforce backward compatibility, and document error codes, rate limits, and SLAs.
Standardize data classification (PII/PHI/confidential/public) and tagging; apply field‑level controls and masking in both code and no‑code forms.
Use consistent integration patterns: event streams for real‑time, CDC/ETL for batch, idempotent endpoints with retries and dead‑letter queues to prevent duplication.
Enforce referential integrity and validation centrally; generate clients/SDKs for code services and no‑code connectors from the same spec.
Security by design
Apply least‑privilege IAM across all services and no‑code connectors: scoped OAuth tokens, per‑resource RBAC, and time‑bound access.
Secrets management with per‑environment keys (Dev/Stage/Prod) via KMS/HSM; never store credentials in no‑code plaintext fields.
Encrypt in transit (TLS 1.2+) and at rest (AES‑256); tokenize or pseudonymize sensitive fields used in experimentation or analytics.
Network controls: IP allowlists for webhooks, egress controls on no‑code tools, private service endpoints, and zero‑trust policies for internal tools.
Secure build paths on both sides: SAST/DAST for code; app/connector permission reviews and marketplace vetting for no‑code; dependency and plugin audits.
Session and auth standards: SSO (SAML/OIDC), SCIM for provisioning, short‑lived tokens, device/session timeouts, and MFA for admin roles.
Compliance and audit
Map data flows end‑to‑end for PII/PHI; maintain a Record of Processing Activities (RoPA) and data inventory with systems, subprocessors, and jurisdictions.
Align retention and deletion across stacks; automate legal holds and data subject request workflows (access, delete, rectify) through shared services.
Execute DPAs and BAAs where applicable; perform vendor risk assessments for no‑code platforms and plugins, including SOC 2 reports and penetration test summaries.
Enforce data residency and localization requirements (e.g., EU, HIPAA); restrict cross‑border transfers and document safeguard mechanisms.
Maintain tamper‑evident audit logs linking code commits, no‑code revisions, approvals, and releases; include “who/what/when/why” with immutable storage.
Run periodic access recertifications and control testing; track corrective actions in a centralized risk register.
Observability
Centralize logs, metrics, and traces from both code services and no‑code events into one observability stack (e.g., OpenTelemetry pipelines).
Propagate correlation/trace IDs across boundaries (front end → no‑code workflow → microservice → datastore) for full request lineage.
Redact sensitive fields at the collector; separate debug vs. audit logs with appropriate retention and access controls.
Monitor data pipelines and syncs: freshness, completeness, and schema drift alerts; validate contracts at deploy time.
Add RUM, synthetic checks, and error tracking to user‑facing flows built in both platforms; define SLOs and error budgets shared by the hybrid team.
Trikon Tech implements this security‑first data architecture - so your hybrid stack stays compliant, observable, and resilient while you scale.
Performance, Reliability, and Scale: Making Hybrid Fast
Hybrid teams hit speed and scale when code developers and no code developers align on a performance‑first blueprint - pushing commodity work to the edge and offloading heavy compute to code services, while keeping delivery velocity high.
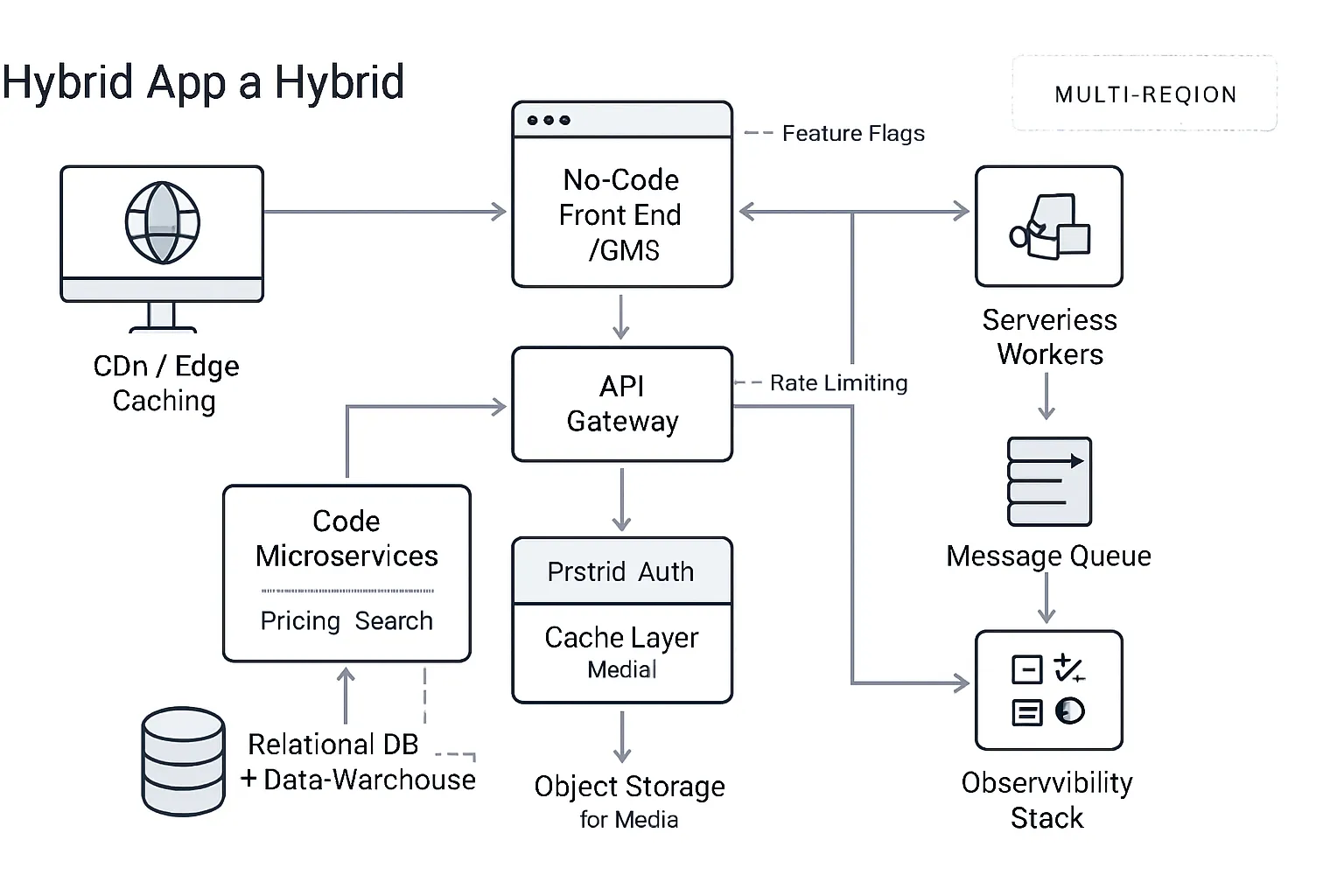
Architecture for speed
Ship static assets through a global CDN with edge caching and smart invalidation; optimize images (next‑gen formats, DPR variants) and prefetch critical routes.
Push personalization and AB logic to the edge where possible; use serverless functions for bursty or geographically distributed workloads.
Buffer spikes with queues for async tasks (emails, webhooks, data syncs) and precompute aggregates to reduce runtime latency.
Layer a cache tier (Redis/edge KV) for session data, feature flags, and hot reads; define cache keys and TTLs per endpoint.
Where no‑code ends and code begins (for performance)
Offload compute‑intensive processes - pricing engines, ML inference, search indexing, batch ETL - to code microservices behind the API gateway.
Keep the no‑code front end focused on orchestration and content; call hardened APIs for heavy logic and data joins.
Use streaming/event topics for real‑time updates; deliver lightweight UI state via no‑code while processing state changes in code services.
Reliability
Define SLOs/SLIs for user‑facing flows across both stacks; track latency, error rate, and availability with shared dashboards.
Implement health checks, timeouts, retries with jitter, and circuit breakers on all inter‑service calls (including no‑code connectors).
Design graceful degradation: fallback content, cached responses, and read‑only modes when dependencies fail; feature flags to disable non‑critical paths.
Run chaos drills and failover tests; deploy multi‑region for critical services with automated disaster recovery runbooks.
Cost visibility
Instrument per‑feature cost: CDN egress, serverless invocations, microservice compute, message queue, database IO, and no‑code plan/overage metrics.
Set budgets and alerts for limits (requests, records, storage) in no‑code platforms; right‑size instances and autoscaling policies for code services.
Prefer event‑driven and serverless for spiky workloads; move hot paths to reserved capacity when steady‑state usage exceeds thresholds.
Track ROI by mapping performance wins to business metrics (conversion, retention) to guide where to optimize next.
Trikon Tech designs and tunes hybrid architectures so you get edge‑level speed, code‑level power, and predictable costs - without slowing delivery.
Collaboration Rituals, Tools, and Documentation
Consistent rituals, a shared toolchain, and living documentation keep code developers and no code developers in sync - so hybrid teams can build and code at speed without sacrificing quality or governance.
Rituals that keep hybrid teams aligned
Weekly roadmap sync (30–45 min)
Inputs: prioritized backlog, capacity, risks, dependencies.
Outputs: committed scope for the week, owners, and explicit trade‑offs.
Tags: no‑code, code, hybrid; flag items with compliance/perf risk.
Bi‑weekly architecture review (60 min)
Review new/changed integrations, API contracts, design tokens, and data models.
Decide on “escape hatches” where no‑code hits limits; capture decisions as ADRs.
Track performance/SLO impacts of choices (latency, cost, reliability).
Demo day (45–60 min)
Show both paths: no‑code flows and code microservices behind them.
Verify acceptance criteria live: UX, a11y, analytics events, and rollback steps.
Capture friction: workarounds, platform gaps, and component drift.
Retro focused on platform friction (45 min)
What slowed us down across stacks? Where did handoffs fail?
Which components need parity updates (design tokens, behaviors)?
Concrete actions: standardize a pattern, add a checklist, update docs.
Optional daily stand‑up (15 min)
Cross‑functional blockers, environment status (Dev/Stage/Prod), and release train alignment.
Shared tooling
One backlog across platforms
Single source of truth for epics/stories with labels: no‑code, code, hybrid, compliance, perf, analytics.
Definition of Done checklist embedded in ticket templates.
Design in Figma with design tokens
Tokens synced to both code and no‑code theming; Storybook as the visual contract.
Specs and contracts
OpenAPI/GraphQL specs with JSON Schema examples; schema registry for versioning and deprecation.
API mocks and contract tests run in CI; Postman collections shared with no‑code builders.
Testing
UI/flow tests in Playwright; API tests in Postman/Newman; synthetic checks for critical journeys.
Visual regression tests for component parity across stacks.
Analytics in a single CDP
One event spec (names, properties, IDs) implemented in both no‑code and code.
Privacy and consent tags enforced at the CDP and downstream tools.
Communication and observability
Shared dashboards (logs, metrics, traces, RUM) with per‑feature views.
Incident channels and runbooks that include both platform owners.
Documentation standards
Living docs hub
Platform limits and “escape hatches” with decision trees (configure vs. build and code).
Component usage examples for both stacks: props/variants, a11y expectations, and theming.
Decision records and checklists
ADR template: context, options, decision, consequences, rollback.
Handoff checklist: user story map, mockups, data model, API spec, test cases, analytics plan, rollout/rollback.
Versioned references
Design tokens, API contracts, and CMS schemas versioned with changelogs.
Clear deprecation timelines and migration guides.
Contribution model
How to propose a token/component change; required reviews (design, accessibility, engineering).
Doc ownership and SLAs for updates.
Training and enablement
Play days and internal clinics
No‑code clinics for code developers: workflow builders, connectors, governance guardrails.
Code clinics for no‑code builders: API patterns, auth basics, performance considerations.
Pairing and shadowing
Rotate ownership on hybrid features to build empathy and shared context.
Self‑serve learning
Short internal courses, sandboxes, and example repos/cloneable no‑code projects.
Certification paths tied to release permissions (e.g., staging‑only until certified).
Readiness metrics
Track time‑to‑first‑merge/publish, escaped defects, and rework due to poor handoffs.
Celebrate wins: faster cycle times, fewer hotfixes, better SLO adherence.
Trikon Tech implements these rituals and tools so your hybrid team stays aligned, moves faster, and documents decisions the right way - every time.
Playbook in Action: Sample Workflows and Outcomes
The fastest teams turn playbooks into muscle memory. Here’s how code developers and no code developers apply this collaboration model to ship high‑confidence outcomes at speed - choosing when to build and code, when to configure, and when to combine.
Scenario 1: Marketing experiment → production feature
Workflow
No‑code landing page + form to validate demand and capture structured data.
Event tracking and analytics wired to a single CDP with clear naming conventions.
Once validated, stand up a code microservice for pricing logic (rules, discounts, geo, tiers) behind the API gateway.
Replace temporary no‑code logic with the service, but keep the no‑code UI and CMS for content velocity.
Shared component library (design tokens + mapped UI) keeps visual parity across both stacks.
Handoffs and controls
Acceptance criteria covers UX/a11y, performance SLAs, analytics events, and rollback.
API contract (OpenAPI) reviewed in an architecture check; feature flag controls for progressive rollout.
Metrics to track
Time‑to‑launch from brief to live.
Conversion lift vs. control.
Handoff time from experiment to productionized service.
Error rate and p95 latency of pricing calls under peak load.
Scenario 2: Internal ops tool with external‑facing extension
Workflow
Build the CRUD ops tool in no‑code (lists, forms, approvals) for rapid iteration.
Expose a secure code API with rate limits, RBAC, and audit trails; connect no‑code via scoped credentials.
Later, publish selected operations to customers via a code front end (Next.js/React) that calls the same API.
Keep internal content, playbooks, and FAQs in the no‑code CMS; external surface uses shared tokens/components for parity.
Handoffs and controls
Data model and validation centralized; schema changes gated with RFCs.
Integration tests (Postman/Newman) plus Playwright flows for both internal and external paths.
Metrics to track
Error rate reduction after API hardening.
Task automation hours saved per team per month.
First‑response and resolution time for ops tickets.
P95 latency and success rate of public endpoints.
Scenario 3: Progressive decoupling from a monolithic no‑code app
Workflow
Identify bottlenecks and cost drivers; plan a phased migration.
Extract auth, billing, and reporting into code services (auth service, billing gateway, reporting pipeline).
Keep the no‑code UI and content management for velocity; swap heavy logic for API calls.
Use feature flags to shadow‑run both implementations; compare metrics before switching traffic.
Handoffs and controls
Versioned API contracts and schema registry to prevent drift.
SLOs set for new services; circuit breakers and graceful fallback in the UI.
Metrics to track
Cost reduction across platform and infrastructure lines.
Performance gains (p95 latency, throughput) on critical flows.
Deploy frequency and change failure rate post‑decoupling.
Time to restore with one‑click rollback/version restore.
What great looks like
Stable release cadence with clear release trains and emergency lanes.
Fewer Sev‑1 incidents through SLOs, circuit breakers, and validated rollback plans.
Clear ownership and decision rights reflected in a living RACI and shared dashboards.
Visible cycle‑time improvements: faster idea‑to‑impact while keeping compliance and performance intact.
Consistent UX and brand fidelity via shared design tokens and component parity - regardless of where teams build and code.
Trikon Tech operationalizes these workflows end‑to‑end - so your hybrid team moves from experiment to enterprise‑grade with confidence, speed, and measurable outcomes.
Conclusion: Ship Faster Together with Trikon Tech
Hybrid teams win when code developers and no code developers share one operating model, one backlog, and one definition of done. Trikon Tech turns that collaboration into momentum - so you can build and code what differentiates, configure what accelerates, and ship faster with confidence.
Why partner with Trikon Tech
Trikon Tech’s Discover → Plan → Build process aligns code developers and no code developers around business outcomes.
Rapid build cycles, reduced costs, founder control, scalable growth, and practical data mastery.
Your next step
Bring your roadmap; we’ll help you pick the right blend of build and code + no‑code, set up shared libraries, and establish governance that scales.
Start a discovery call at Trikon.Tech to accelerate your hybrid delivery and ship with confidence.
